The Internet of Things (IoT) has revolutionized the way we live and work. From smart homes to industrial automation, IoT devices have become an integral part of our daily lives. However, this growing reliance on IoT also brings with it a multitude of security risks that can expose sensitive data, disrupt operations, and even pose physical threats.
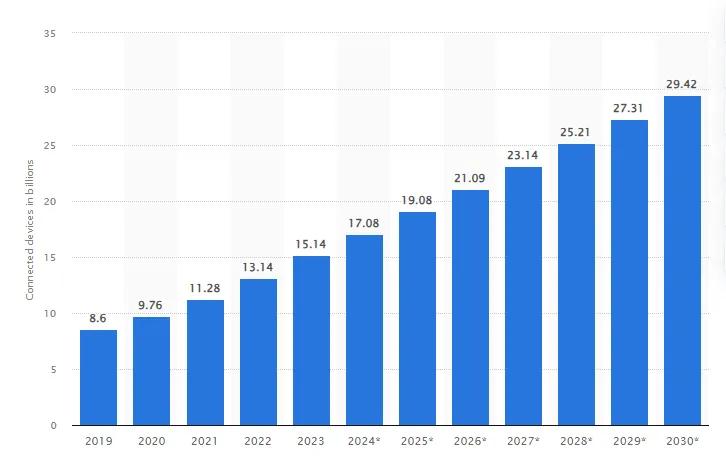
Statista forecasts that the number of IoT devices will surge to over 29 billion by 2030, while the market for IoT end-user solutions is projected to reach approximately $1.6 trillion by 2025.
This exponential growth, coupled with the increasing complexity of IoT ecosystems, has made securing these devices a critical challenge. A report by Kaspersky indicates that 43% of businesses have not fully protected their IoT infrastructure.
The consequences of IoT security breaches can be far-reaching. In 2016, a cyberattack on Mirai, a botnet composed of IoT devices, resulted in a massive distributed denial-of-service (DDoS) attack that disrupted internet service for millions of users. In 2022, over 112 million IoT devices were targeted by cyberattacks worldwide, resulting in data breaches, disruptions to critical infrastructure, and even physical damage to property.
To address these escalating risks, it is imperative to understand the common vulnerabilities that plague IoT devices and implement effective security measures. Let’s explore the top 10 IoT device vulnerabilities and explore strategies to mitigate them.
What is the Internet of Things (IoT)?
The Internet of Things (IoT) encompasses physical objects embedded with sensors and actuators that are connected to computing systems via wired or wireless networks. IoT devices are designed to make our lives easier by automating tasks, providing real-time data, and improving efficiency. The IoT has the potential to revolutionize the way we live and work, from smart homes to smart cities.
What are IoT devices?
IoT devices are the building blocks of the Internet of Things ecosystem. These are typically everyday objects equipped with computing devices such as sensors, processors, and communication hardware. These devices collect, transmit, and act on data they acquire from their environments. Sensors in an IoT device might track everything from temperature and light levels to motion or air quality. The actuators then respond to this data, often triggering a response like adjusting the thermostat or sending an alert.
IoT devices vary widely in complexity and purpose. They can be as simple as a smart thermostat in a home or as complex as a smart factory machine with hundreds of sensors monitoring performance and efficiency. Common examples include wearable health monitors, smart home appliances, and connected cars. In industrial settings, IoT devices might be used for predictive maintenance of machinery or to optimize supply chain logistics.
What are the Challenges of IoT?
One of the biggest challenges of IoT is the sheer number of devices that are connected to the internet. With so many connected devices communicating with each other, it can be difficult to manage and secure them all. Additionally, many IoT devices have limited computational abilities, which leaves minimal space for the robust data protection and security required to defend against cyberattacks.
Another challenge of IoT is the varied transmission technology used by IoT devices. This makes it challenging to implement sufficient security methods and protocols. Furthermore, the basic components of IoT devices are often vulnerable, which leaves millions of smart devices open to attack.
Why are IoT devices vulnerable?
IoT devices often face vulnerabilities, primarily due to the absence of adequate built-in security measures to combat potential threats. Beyond the technical vulnerabilities, user behavior also plays a role in increasing the susceptibility of these devices to various risks. Below are several key factors contributing to the ongoing vulnerability of these smart devices:
- Limited computational abilities and hardware limitations: IoT devices have specific functions that warrant only limited computational abilities, leaving little room for robust security mechanisms and data protection.
- Heterogeneous transmission technology: IoT devices frequently employ a range of transmission technologies. This diversity complicates the development of uniform security measures and protocols.
- Components of the device are vulnerable: Vulnerable basic components affect millions of deployed smart devices.
- Users lacking security awareness: The limited awareness of users regarding security can leave smart devices open to vulnerabilities and potential attacks.
How IoT Device Vulnerabilities Affect Users
IoT devices are vulnerable to various cyber threats, including malware, ransomware, and distributed denial-of-service (DDoS) attacks. Cybercriminals exploit security weaknesses in IoT devices to initiate attacks on both organizations and individual users. A compromised device poses a threat to IoT security by granting cybercriminals access to interconnected networks. This access can lead to the theft of crucial corporate data, login details, financial information, and other sensitive data. This information can be used to commit identity theft, fraud, and other cybercrime. Examples of how IoT device vulnerabilities can affect users include:
- Lateral network movement: Cyber criminals can use the initial breach of a vulnerable device to move deeper into corporate networks. An attacker looks to exploit a vulnerability in a machine and then escalate their privileges. They then use lateral movement to reach critical data and spread malware through a network.
- IoT botnets: Cyber criminals use botnets, which are large networks of devices, such as routers, to launch large-scale cyberattacks like distributed denial-of-service (DDoS) attacks. Botnets pool multiple infected devices managed from a command-and-control (C&C) server.
- Evolving botnets: The growth of the IoT poses a risk of botnets evolving and becoming an even more significant threat to users. This could happen through peer-to-peer (P2P) file-sharing technologies that enable attackers to connect devices without requiring a central server, making prevention near-impossible.
How IoT Device Risks Affect Organizations
Organizations face significant risks from IoT device vulnerabilities. A single vulnerable device can give cyber criminals access to an entire network, putting sensitive data and critical systems at risk. Examples of how IoT device vulnerabilities can affect organizations include:
- Cybercriminals can use IoT device vulnerabilities to access sensitive data, such as customer information, financial data, and intellectual property. This can lead to significant financial losses, legal liabilities, and reputational damage.
- IoT device vulnerabilities can cause operational disruptions, such as system failures and downtime. This can lead to lost productivity, missed deadlines, and lost revenue.
- Organizations are required to adhere to multiple regulations, including the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). Vulnerabilities in IoT devices can result in non-compliance, potentially leading to substantial penalties and legal responsibilities.
What are the Compliance Frameworks for IoT Security?
As the adoption of IoT devices continues to grow, so does the need for standardized security frameworks to protect these devices and the data they generate. Compliance frameworks provide a comprehensive set of guidelines and best practices for organizations to manage IoT security risks and demonstrate adherence to industry standards.
Top Compliance Frameworks for IoT Security
- IoT Security Assurance Framework (IoTSAF): Developed by the IoT Security Foundation (IoTSF), the IoTSAF is a risk-based framework that provides a comprehensive approach to IoT security. It covers all aspects of IoT security, from device design and development to deployment and operation.
- CSA IoT Cybersecurity Framework: The CSA IoT Cybersecurity Framework, developed by the Cloud Security Alliance (CSA), focuses on securing IoT devices and systems in the cloud environment. It provides guidelines for cloud providers, device manufacturers, and solution providers to enhance IoT security in cloud-based deployments.
- NIST Cybersecurity Framework for IoT: The NIST Cybersecurity Framework for IoT, developed by the National Institute of Standards and Technology (NIST), provides a comprehensive framework for managing IoT cybersecurity risks. It outlines a set of core functions and categories that organizations can use to assess, prioritize, and mitigate IoT security risks.
- ISA/IEC 62443: ISA/IEC 62443 is a series of international standards for industrial automation and control systems (IACS) cybersecurity. While not specifically focused on IoT, it provides valuable guidance for securing IACS devices, often including IoT components.
What are the Top IoT Vulnerabilities that Make Devices Insecure?
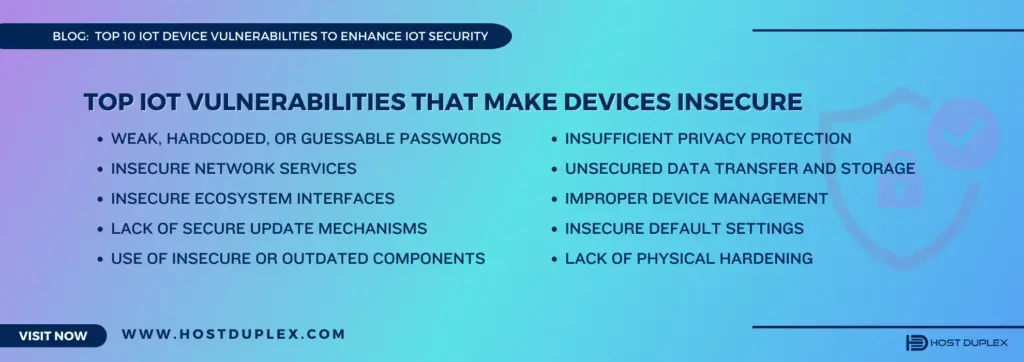
1. Weak, Hardcoded, or Guessable Passwords
When it comes to IoT device security, weak or default passwords are a significant threat to IoT security. Attackers can use brute-force attacks to guess passwords or use publicly available or unchangeable credentials to gain unauthorized access to the device. Once attackers gain access to the device, they can steal sensitive data, manipulate device functionality, or use the device as a gateway to launch attacks on other devices in the network.
2. Insecure Network Services
Insecure network services are one of the most common vulnerabilities in IoT devices. Attackers can exploit them to gain unauthorized access to the device and its data. Insecure network services can also be used to launch attacks on other devices and networks. There are several types of insecure network services that can be found in IoT devices, including:
- Unsecured network protocols: Many IoT devices use unsecured network protocols such as HTTP, FTP, and Telnet. These protocols transmit data in plain text, which can be intercepted and read by attackers. Attackers can use this information to gain unauthorized access to the device or to launch attacks on other devices and networks.
- Unsecured network services: Many IoT devices have unsecured network services such as SSH, SNMP, and UPnP. These services can be exploited by attackers to gain unauthorized access to the device or to launch attacks on other devices and networks.
- Unsecured web interfaces: Many IoT devices have web interfaces that are not secured properly. These interfaces can be exploited by attackers to gain unauthorized access to the device or to launch attacks on other devices and networks.
- Unsecured cloud services: Many IoT devices use cloud services to store and process data. These services can be exploited by attackers to gain unauthorized access to the device or to launch attacks on other devices and networks.
3. Insecure Ecosystem Interfaces
Insecure ecosystem interfaces are one of the top 10 vulnerabilities that make IoT devices insecure. These interfaces refer to the web, backend API, cloud, or mobile interfaces in the ecosystem outside of the device that allows compromise of the device or its related components. Common issues include a lack of authentication/authorization, a lack or weak encryption, and a lack of input and output filtering.
4. Lack of Secure Update Mechanisms
Devices that have unsecured update mechanisms are at risk of installing harmful or unauthorized code, firmware, and software. Such compromised updates can undermine the integrity of IoT devices, posing significant risks, especially for critical sectors like energy, healthcare, and industry.
Without secure update mechanisms, software and firmware updates can actually put devices at risk. These risks include:
- Unauthorized Device Firmware Updates: Attackers can exploit insecure update mechanisms to inject malicious firmware onto IoT devices, effectively taking control of them. This can lead to data breaches, device hijacking, and disruption of critical operations.
- Man-in-the-Middle (MitM) Attacks: Insecure update mechanisms can allow attackers to intercept and modify update packets, introducing vulnerabilities or backdoors into the device’s firmware.
- Outdated Firmware: Without a secure update mechanism, it becomes challenging to deploy critical security patches and updates, leaving devices vulnerable to known exploits.
- Lack of Anti-Rollback Mechanisms: Without anti-rollback mechanisms, attackers can downgrade the firmware to a more vulnerable version, undoing security advancements and exposing the device to previously patched vulnerabilities.
5. Use of Insecure or Outdated Components
IoT devices often rely on a multitude of hardware and software components, including sensors, microcontrollers, communication protocols, and operating systems. These components can be vulnerable if they are not properly maintained or if they contain security flaws.
The following are some of the most common insecure or outdated components that can be found in IoT devices:
- Operating Systems: Many IoT devices use outdated operating systems that the manufacturer no longer supports. This can leave the device vulnerable to attacks that exploit known vulnerabilities in the operating system.
- Firmware: Firmware is the software that runs on the device’s hardware. Outdated firmware can contain security vulnerabilities that can be exploited by cybercriminals.
- Web Interfaces: Many IoT devices have web interfaces that allow users to interact with the device. These web interfaces can be vulnerable to attacks such as cross-site scripting (XSS) and SQL injection.
- Encryption: Encryption is used to protect data that is transmitted between the device and other systems. Cybercriminals can easily break weak encryption, leaving the data vulnerable to interception and theft.
- Authentication: Authentication is the process of verifying a user’s or device’s identity. Weak authentication mechanisms can allow cybercriminals to access the device and its data.
6. Insufficient Privacy Protection
Insufficient privacy protection is one of the top IoT vulnerabilities. Personal information stored on IoT devices or in the ecosystem is often collected insecurely, improperly, or without permission. This personal data can range from medical information to power consumption and driving behavior. Lack of appropriate controls will jeopardize users’ privacy and can have legal consequences.
With the highly valuable nature of a user’s sensitive personal information, privacy protection is essential in our connected world. Many connected devices collect personal data that needs to be securely stored and processed to remain compliant with various privacy regulations, including Europe’s General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA).
7. Unsecured Data Transfer and Storage
Insecure data transfer and storage is one of the most critical vulnerabilities in IoT. Lack of encryption or access control of sensitive data anywhere within the ecosystem, including at rest, in transit, or during processing, can lead to significant data loss. This data is often used in automated decision-making and to control devices, making it critical that it remains protected as information is transferred across the network or stored in a new location.
8. Improper Device Management
Inadequate device management is one of the most critical vulnerabilities in IoT. Lack of security support on devices deployed in production, including asset management, update management, secure decommissioning, systems monitoring, and response capabilities, can lead to unauthorized access to corporate networks and interception of traffic and information.
Managing all devices throughout their lifecycle is a significant challenge in the IoT ecosystem. The provisioning, operation, and updating of devices are key concerns of IoT device management. The discovery and identification of IoT devices is a necessary first step in monitoring and protecting these devices. Traditional IoT device identification using IP addresses and underlying operating systems doesn’t work for the IoT.
9. Insecure default settings
IoT devices and systems are frequently shipped with default configurations that are not only insecure but also restrict operators from modifying them to enhance security. This fundamental flaw presents a two-fold risk:
- Hardcoded Weaknesses: Devices often come with hardcoded default passwords, hidden backdoors, and other vulnerabilities embedded in their firmware. These weaknesses are easily exploitable by attackers, essentially providing them with a “hall pass” to access and manipulate the device.
- Difficulty in Modification: The default settings are typically challenging for users to change. This limitation not only makes the devices more vulnerable but also hinders the implementation of stronger security measures.
10. Lack of Physical Hardening
One of the most overlooked aspects is the lack of physical hardening of these devices. Physical hardening refers to the measures taken to protect a device from physical tampering or manipulation.
IoT devices are often deployed in remote or dispersed environments, making them vulnerable to attacks that target their physical components. Attackers gaining physical access to these devices can extract sensitive information, which can be used to facilitate future remote attacks or to take direct control of the device. This vulnerability is particularly concerning because it can lead to the disruption of critical services. For instance, if an attacker were to tamper with the physical layer of a sensor designed to detect fire, flood, or unexpected motion, it could prevent the sensor from performing its essential functions.
The heart of the issue lies in the fact that many IoT devices lack the necessary built-in security features to counter physical threats. While there are robust security protocols to protect data in transit, the data stored on the device itself often remains unprotected. This oversight can have serious implications, especially considering the nature of the data these devices handle and the essential services they provide.
What are the Best Practices to Secure IoT Devices?
Organizations can significantly reduce the risk of IoT device security breaches and protect their valuable data and assets by implementing the following practices:
- Implement strong password policies: Enforce the use of strong, unique passwords for all IoT devices. Avoid using default passwords and enable password complexity requirements.
- Enable network encryption: Ensure that IoT devices communicate over encrypted networks, such as WPA2-PSK or WPA3 for Wi-Fi. Avoid using unencrypted networks that expose data to eavesdropping.
- Maintain software updates: Regularly check for and install software updates for IoT devices. Apply updates promptly to patch known vulnerabilities and enhance security.
- Secure firmware updates: Obtain firmware updates from trusted sources, verify their integrity, and implement secure firmware update mechanisms to prevent unauthorized modifications
- Enforce physical security measures: Restrict physical access to IoT devices and implement access control mechanisms. Secure physical environments to prevent unauthorized access and tampering
- Adopt secure coding practices: Follow secure coding guidelines and best practices during IoT device development and minimize the introduction of vulnerabilities through rigorous code testing and review.
- Verify supply chain security: Implement measures to verify the security of the supply chain for IoT devices and collaborate with suppliers to ensure the integrity and security of devices throughout the supply chain.
- Implement device authentication: Enforce strong authentication mechanisms, such as digital certificates or tokens, and verify the identity of devices before allowing them to join the network.
- Protect data privacy: Implement data encryption and access controls to protect sensitive data collected by IoT devices. Establish data privacy policies and procedures to ensure compliance with data protection regulations.
- Raise security awareness: Educate users about the security risks associated with IoT devices and provide clear guidance on protecting IoT devices and securing personal data.
Additional considerations
- Separate IoT devices from other network segments to limit the potential impact of a security breach.
- Implement a security gateway to monitor and control traffic between IoT devices and the rest of the network.
- Use vulnerability scanning tools to identify and remediate vulnerabilities in IoT devices.
- Have a plan in place to respond to security incidents involving IoT devices.
Bottom Line
The vulnerabilities inherent in IoT devices pose significant risks to data privacy, operational continuity, and even physical safety. Embracing a culture of cybersecurity, adopting industry-recognized compliance frameworks, and fostering continuous security monitoring are essential steps in ensuring a resilient and secure IoT ecosystem.


Top 10 IoT Device Vulnerabilities to Enhance IoT Security