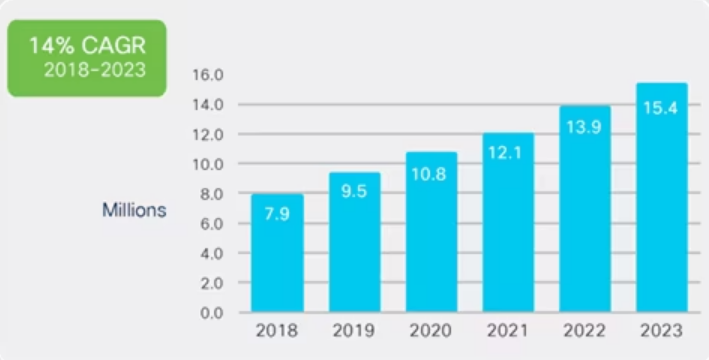
DDoS attacks, or distributed denial-of-service attacks, have become an increasingly common threat to organizations of all sizes. These attacks are not a new phenomenon, but their frequency and sophistication are what make them so concerning. According to Cisco, the number of DDoS attacks worldwide per year is expected to double, from 7.9 million in 2018 to 15.4 million in 2023. This represents an alarming 807% increase in DDoS attacks.
These attacks have the potential to cripple a company’s network infrastructure, rendering websites and online services inaccessible to legitimate users. This can result in significant financial losses, reputational damage, and a loss of customer trust. Furthermore, DDoS attacks can be used as a smokescreen to divert security teams’ attention away from other cyberattacks, such as data breaches or malware infections.
DDoS attacks are becoming more sophisticated and powerful, making them more difficult to counter. Attackers are constantly coming up with new ways to overwhelm targeted networks. Additionally, the rise of botnets and the availability of DDoS-for-hire services have made it easier for attackers to launch large-scale attacks.
Companies can no longer afford to be naive to DDoS attacks. A proactive approach to DDoS defense is required to protect against these attacks. To stay one step ahead of attackers, this proactive approach requires implementing robust security measures as well as regularly testing and updating defenses.
What are denial of service (DDoS) attacks?
A distributed denial-of-service attack (DDoS) is a type of cyberattack that attempts to disrupt normal traffic on a targeted network, service, or server by flooding it with Internet traffic. In other words, a DDoS attack is akin to an unexpected traffic jam on the highway, preventing regular traffic from reaching its destination.
How do DDoS attacks work?
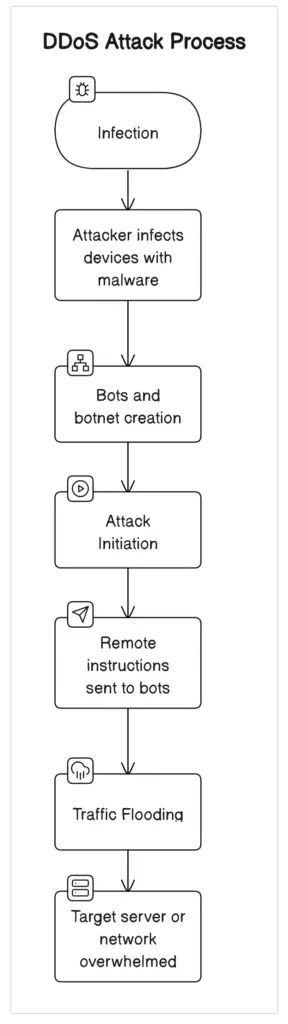
Usually, denial-of-service (DDoS) attacks start with the formation of a botnet. This network consists of a variety of compromised IoT devices, such as computers, including servers, laptops, mobile devices, and PCs. These computers have malware on them, which gives the attacker control over them and allows them to direct traffic to the intended destination.
These compromised devices flood the target with an excessive amount of traffic once the botnet is established. This might include a mix of HTTP requests, connection requests, or malicious packets, all aimed at overloading the target’s ability to manage valid traffic.
The target server or network resource is flooded by the sheer volume of malicious traffic. A denial of service occurs when the server is overloaded to the point where it is unable to respond to valid traffic. This means that legitimate users are unable to access the website or service.
What are the types of DDoS attacks?

Based on their nature, DDoS attacks can be categorized into the following types:
1. Volumetric attacks
Volumetric attack is the most common type of DDoS attack and aims to overwhelm the target network or website with a massive amount of traffic, making it impossible for legitimate traffic to get through. Volumetric attacks are usually carried out using botnets, which are networks of compromised computers that are controlled by the attacker.
2. Protocol attacks
A protocol attack, a.k.a computational attack, targets the network infrastructure of the target website or network. They exploit vulnerabilities in the network protocols to consume the processing capacity of network infrastructure resources like servers, firewalls, and load balancers. Protocol attacks can be carried out using a variety of techniques, including SYN floods, UDP floods, and ICMP floods.
3. Application attacks
These attacks target the application layer of the target website or network. They exploit vulnerabilities in the application layer to consume finite resources like disk space and available memory. Application attacks can be carried out using a variety of techniques, including HTTP GET floods, TLS renegotiation, and direct DNS queries. While DNS reflection floods the target’s internet connection, direct DNS queries aim to overload the target’s DNS infrastructure, denying legitimate requests the ability to resolve domain names
4. Multiple Vector Attacks
These attacks combine multiple methods from the previously mentioned types. They are increasingly common and are known for their complexity and effectiveness. There has been a significant 83% increase in multi-vector attacks in Q3 2023 compared to the same period in 2022. These attacks often target multiple protocols or system components, making them more challenging to mitigate.
How to Detect DDoS Attacks?
Detecting a DDoS attack promptly is important to minimize its impact. Sadly, it can be challenging to distinguish from normal surges in network or web traffic and DDoS attacks. It is getting harder and harder to detect these attacks, especially when more sophisticated methods like Generative Adversarial Networks (GANs) are being used. GANs can imitate real user requests.
You can monitor your network traffic and look for any of the following red flags that can indicate a potential DDoS attack:
- Excessive connection requests from specific IP addresses.
- Server responses with a 503 unavailable error due to service outages.
- Repetitive traffic source addresses querying the same data beyond its TTL.
- Slow site performance reported by internal users.
- Unexplained spikes in traffic visible in Google Analytics reports
While constant traffic monitoring is necessary for early detection, setting too many alerts can lead to ‘alert fatigue,’ causing IT teams to overlook critical signals among numerous harmless events. Some traditional advanced detection methods and more recent advancements can help you identify a DDoS attack effectively:
Conventional Techniques for DDoS Detection
Flow-based Analysis
This technique looks closely at network traffic flows to identify any odd trends that might point to a DDoS attack. Flow-based analysis assists in identifying large-scale anomalies that are typical of DDoS attacks by monitoring the volume, frequency, and type of network traffic.
Packet-based Analysis
Packet-based analysis involves analyzing individual packets to identify patterns and anomalies. This method can help detect DDoS attacks by identifying packets that are part of the attack traffic.
Behavioral Analysis
Behavioral analysis can identify anomalies in network traffic by examining how it behaves over time. This approach is very useful for detecting slow-rate DDoS attacks, which other approaches that concentrate on volume spikes may miss.
Anomaly Detection
Anomaly detection leverages machine learning algorithms to learn what ‘normal’ traffic looks like and then identifies deviations. This approach can adapt to changing traffic patterns, making it a powerful tool for detecting new and evolving DDoS tactics.
Signature-based Detection
This technique uses predefined signatures or patterns to identify known DDoS attacks. While effective against familiar threats, it can be less useful in spotting new attack methodologies.
Cloud-based detection
This method uses cloud computing services to provide scalable and reliable DDoS detection and mitigation. Cloud-based detection can be done using various tools, such as cloud service providers, cloud security services, and cloud-based DDoS protection services. Cloud-based detection can help reduce the burden on the target network or server, as well as provide a higher level of security and availability.
Intrusion Prevention Systems and Intrusion Detection Systems (IPS/IDS)
Security technologies like intrusion detection systems (IDS) and intrusion prevention systems (IPS) keep an eye on network traffic and guard against possible attacks. IDS keeps an eye on network traffic and alerts the administrator to any unusual or suspicious activity. IPS, on the other hand, performs all of those tasks in addition to putting automated responses in place to lock the intruder out and safeguard systems from being taken over or data being stolen. SolarWinds Security Event Manager, ManageEngine EventLog Analyzer, ManageEngine Log360, ESET Protect, Snort, and OSSEC are some popular IDS/IPS software available in the market.
Recent Advancements
Machine Learning-Based Approaches
Advanced machine learning models, like the LSTM (Long Short-Term Memory) network, represent a significant leap in DDoS detection. Developed by researchers at Institut Polytechnique de Paris, this approach uses one model to identify adversarial traffic and another to confirm a DDoS attack, offering high adaptability and accuracy.
AI-Enhanced Firewalls
Modern firewalls, augmented with AI, are at the forefront of network defense. They analyze incoming and outgoing traffic, distinguishing between benign and malicious requests based on complex behavior patterns, learned signatures, and real-time analysis.
In-Line and Out-Of-Band Monitoring
In-line monitoring tools are embedded directly in the network, actively filtering malicious traffic. Out-of-band monitoring, on the other hand, analyzes copies of network traffic, providing comprehensive insights into traffic patterns and anomalies without impacting network performance.
Web Scanners and WAF (Web Application Firewalls)
Focused on protecting web applications, these tools employ machine learning algorithms to scrutinize and filter web traffic. They are instrumental in identifying and blocking bots and other malicious actors, safeguarding against application-layer DDoS attacks.
Responding to a DDoS Attack
When confronted with a Distributed Denial of Service (DDoS) attack, quick and strategic action is required to limit damage and restore services. This section will discuss key response strategies for effectively countering a DDoS attack, focusing on practical and immediate actions.
Immediate Detection and Assessment
- Utilize real-time monitoring to identify unusual spikes or patterns in network traffic that may indicate a DDoS attack.
- Quickly assess the scale and type of attack to determine the appropriate response.
Engage Mitigation Protocols
- Identify and block IP addresses that are sources of malicious traffic.
- Implement rate limiting to prevent your server from being overwhelmed by excessive requests.
- Distribute traffic evenly across multiple servers to reduce the load on any single server.
- Utilize CDNs to absorb and distribute large volumes of traffic, mitigating the impact on your primary servers.
- Use web application firewalls (WAFs) to filter out malicious traffic while allowing legitimate traffic through.
- Redirect malicious traffic to a null route or ‘blackhole’, effectively discarding the traffic before it reaches your network.
Coordinate with External Partners
- Your Internet Service Provider can provide assistance in mitigating the attack, such as rerouting traffic or providing additional bandwidth.
- Work together with ISPs and hosting providers for a coordinated response to the attack.
Post-Attack Actions
- After mitigating the attack, conduct a thorough analysis to understand its nature and origin.
- Depending on the severity and nature of the attack, report the incident to relevant authorities and document all findings for future reference.
- Keep internal teams and external stakeholders informed about the attack and the measures taken to resolve it.
Best practices for preventing DDoS attacks
1. Know your network’s traffic
The first step in preventing DDoS attacks is to understand your network’s traffic patterns. This will help you identify any unusual traffic that could be a sign of an attack. You can use network monitoring tools to track your network’s traffic and identify any anomalies. Once you have identified unusual traffic, you can take steps to block it and prevent it from causing damage.
2. Create a DDoS response plan
It’s important to have a plan in place to respond to DDoS attacks. This plan should include steps to take when an attack is detected, such as blocking traffic from the source of the attack and notifying relevant parties. The plan should also include procedures for restoring normal operations after an attack.
3. Make your network resilient
To make your network resilient to DDoS attacks, you can take several steps. One of the most important is to ensure that your network has sufficient bandwidth to handle large amounts of traffic. You can also use load balancers to distribute traffic across multiple servers, which can help prevent any one server from being overwhelmed. Additionally, you can use firewalls and intrusion prevention systems to block traffic from known malicious sources.
4. Practice good cyber hygiene
Good cyber hygiene practices can help prevent DDoS attacks. These include:
- Changing passwords frequently
- Regularly scanning for vulnerabilities and patching any vulnerabilities that are found
- Deploying anti-malware and DDoS protection solutions and services
- Deploying firewalls with up-to-date access control lists
5. Scale up your bandwidth
Scaling up your bandwidth can help you handle large amounts of traffic during a DDoS attack. You can work with your internet service provider (ISP) to increase your bandwidth or use a content delivery network (CDN) to distribute traffic across multiple servers. This can help prevent any one server from being overwhelmed by traffic.
6. Use anti-DDoS hardware and software
Anti-DDoS hardware and software can help protect your network from DDoS attacks. These solutions can detect and block malicious traffic before it reaches your network, preventing it from causing damage. Some examples of anti-DDoS hardware and software include firewalls, intrusion prevention systems (IPSs), and intrusion detection systems (IDSs).
7. Move to the cloud
Moving your network to the cloud can help protect it from DDoS attacks. Cloud service providers have the resources and expertise to handle large amounts of traffic, which can help prevent your network from being overwhelmed during an attack. Additionally, cloud providers often have built-in DDoS protection services that can help detect and block malicious traffic.
8. Implement sound network monitoring practices
Implementing sound network monitoring practices can help you detect and respond to DDoS attacks quickly. You can use network traffic analysis tools to identify the source of an attack and take steps to block it. Some examples of network traffic analysis tools include:
- SolarWinds NetFlow Traffic Analyzer
- ManageEngine OpManager Plus
- Noction Flow Analyzer
- Elastic Stack
- Plixer Scrutinize
- Open WIPS-NG
9. Use a content delivery network (CDN)
When a DDoS attack occurs, it can overwhelm your servers with traffic, causing them to crash and become unavailable. By using a CDN, you can distribute the traffic across multiple servers, reducing the load on any one server and preventing it from being overwhelmed. This can help keep your website up and running during a DDoS attack and prevent it from being taken offline.
Some examples of CDN providers include:
10. Implement rate limiting
Rate limiting is a technique used to limit the number of requests that a server will accept from a single IP address or user. By implementing rate limiting, you can prevent a single user or IP address from overwhelming your server with requests and causing it to crash. Rate limiting can be implemented at various levels, including the network, application, and API levels.
Some common rate-limiting techniques include:
- Token bucket: This technique uses a token bucket to limit the number of requests that can be made over a given period of time. Each request consumes a token, and once the tokens are depleted, no more requests can be made until the bucket is refilled.
- Leaky bucket: This technique limits the rate of requests by allowing a fixed number of requests to be made over a given period of time. Requests that exceed the limit are dropped or delayed.
- Sliding window: This technique limits the rate of requests by allowing a fixed number of requests to be made within a sliding window of time. The window moves forward as requests are made, and requests that exceed the limit are dropped or delayed.
11. Use web application firewalls (WAFs)
A web application firewall (WAF) is a security solution that can help protect your web applications from various types of attacks, including DDoS attacks. A WAF, like one provided by Cloudflare and AWS, sits between your web application and the internet and can inspect incoming traffic for malicious activity. If a request is deemed malicious, the WAF can block it before it reaches your web application.
12. Use a dedicated DDoS protection service
A dedicated DDoS protection service can help protect your network devices from DDoS attacks by providing specialized hardware and software solutions. Some common features of DDoS protection services include:
- Traffic scrubbing: This technique involves filtering incoming traffic to remove malicious traffic and allow legitimate traffic to pass through.
- Anycast routing: This technique involves routing traffic to the nearest server in a network of servers, reducing latency and improving performance.
13. Use a honeypot
A honeypot is a security mechanism that can be used to detect and respond to DDoS attacks. A honeypot is a decoy system that is designed to look like a legitimate target. When an attacker targets the honeypot, the system can detect the attack and alert you to the threat.
14. Educate employees on how not to become a bot
DDoS attacks often use botnets to carry out the attack. Botnets are networks of infected devices that can be controlled remotely by an attacker. To prevent your employees from becoming part of a botnet, you should educate them on how to avoid becoming infected with malware. This includes:
- Avoiding suspicious emails and attachments
- Using strong and unique passwords
- Keeping software up to date
- Using reputable anti-malware solutions
- Using reputable VPNs
Bottom Line
DDoS attacks pose a significant threat to organizations of all sizes. Organizations can effectively shield themselves from future attacks by understanding the nature of DDoS attacks, implementing effective detection and mitigation strategies, and adopting a proactive approach to cybersecurity. Remember, vigilance and continuous adaptation are key to staying ahead of the ever-changing DDoS threat landscape.



How to Detect and Respond to DDOS Attacks (Distributed Denial of Service)