The omnipresence of cyber threats has become a significant concern for organizations worldwide. A notable 48% of organizations reported an increase in cyberattacks in 2023 compared to the previous year. Cyber threats are not just increasing in number but also evolving in sophistication. From ransomware attacks to business email compromise attacks, cybercriminals are leveraging every weak point for valuable data and financial gains.
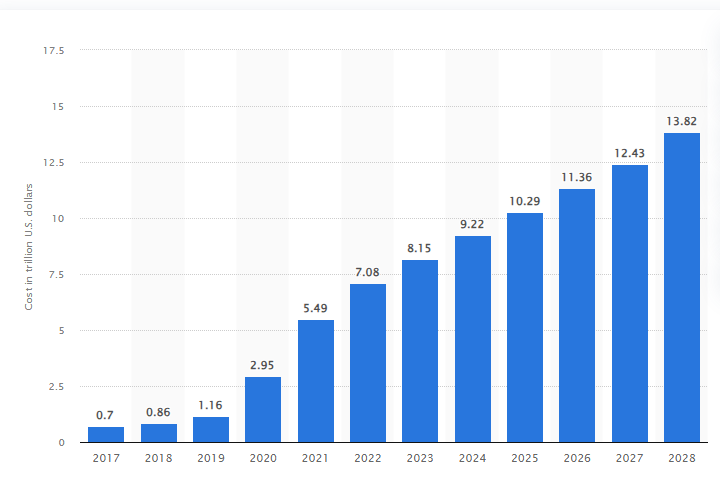
According to Statista, the estimated cost of cybercrime in the global cybersecurity market is projected to witness a substantial rise over the next five years, culminating in a total increase of 5.7 trillion U.S. dollars, which translates to a significant growth of 69.94 percent. This trend marks the eleventh consecutive year of increasing cybercrime costs.
So, where does this leave organizations in their quest for cybersecurity? The traditional method of categorizing cyber risks as high, medium, or low is now outdated and subjective. Different perceptions of risk severity between individuals and management can lead to misunderstandings and inadequate responses to cyber threats. For instance, when multiple risks are all labeled as ‘medium’, it becomes challenging to prioritize them and decide on resource allocation, often resulting in a strategic impasse without a clear path forward.
The solution lies not just in the implementation of advanced technologies but also in a fundamental change in perspective. We need to move from a reactive stance to a proactive, predictive approach.
Now, imagine a shift in perspective. What if you could say, “Our analysis shows that a breach could potentially cost us $5 million, with a 70% likelihood of occurring within the next year”? This isn’t just a hypothetical threat; it’s a quantified risk. Such clarity transforms the way decisions are made, from the IT department to the executive boardroom. It turns abstract risks into tangible figures, enabling targeted, effective, and swift decision-making.
Data reveals that business leaders employing cyber risk quantification report significant enhancements in strategic planning and operational efficiency. By assigning numerical values to cyber threats, they effectively strengthen security and better align cybersecurity initiatives with their business objectives.
What is Cyber Risk Quantification (CRQ)?
Cybersecurity risk quantification is the process of evaluating the potential financial impact of a particular cyber threat. It supports intelligent decision-making, helping security professionals make informed decisions about which threats and vulnerabilities to address first.
What sets CRQ apart is its focus on financial risk. Decision-makers and security leaders speak in a language of financial terms, not cybersecurity terminology. The CRQ risk model bridges this gap, helping stakeholders appreciate the value of their security investments without requiring prolonged explanations.
Why is Cyber Risk Quantification Important?
The Cyber Risk Quantification (CRQ) approach empowers security leaders to strategically allocate resources and respond swiftly and effectively to emerging threats. The integration of CRQ into an organization’s cybersecurity strategy yields numerous benefits:
- Bridging the Gap Between Technical and Business Perspectives: CRQ is instrumental in connecting technical cybersecurity discussions with business-centric deliberations. By translating complex cyber risk metrics into financial terms, CRQ enables business leaders to grasp the implications of cyber threats. This common ground aids in aligning security strategies with business objectives, ensuring that technical efforts are directly contributing to the organization’s overarching goals.
- Optimizing Cybersecurity Investments: As a result of CRQ, companies can optimize their investments in cyber risk prevention. By understanding the potential financial loss due to a risk scenario, businesses can make more informed decisions about where to allocate resources for maximum impact.
- Facilitating Clear Communication Across Departments: CRQ improves communication between C-level executives and cybersecurity department heads by introducing a unified language of financial impact. This clarity helps in breaking down silos and promotes a collaborative approach to managing cyber risks, ensuring that all stakeholders have a shared understanding of priorities and strategies.
- Supporting Rigorous Decision-Making: CRQ supports more rigorous decision-making by quantifying the potential financial loss to your business due to a risk scenario. This allows for more accurate project prioritization and risk management.
- Enhancing Organizational Agility: With a comprehensive understanding of the organization’s cyber risk posture, security leaders can respond to emerging threats with greater agility. This proactive approach can significantly reduce the potential impact of cyber threats.
- Compliance and CRQ: Cyber Risk Quantification (CRQ) helps organizations comply with regulatory requirements by quantifying the financial impact of cyber risks, enabling prioritization of controls, demonstrating due diligence, and facilitating effective reporting. Regulators such as the Federal Financial Institutions Examination Council (FFIEC), the European Union’s General Data Protection Regulation (GDPR), and the California Consumer Privacy Act (CCPA) require organizations to manage their cyber risks effectively, and CRQ provides a robust framework for doing so.
Components of Cyber Risk Quantification
Cyber Risk Quantification (CRQ) is a comprehensive process that involves several critical components, each contributing to a thorough understanding and quantification of cyber risks.
Operational Components
Operational components include the following key processes:
- Risk Identification:
- The first step in CRQ is identifying potential cyber risks. This involves understanding the organization’s digital assets, networks, and data and recognizing the various threats they may face, such as malware attacks, data breaches, or insider threats.
- Risk identification also includes recognizing external threats and the evolving nature of cybercrime and tactics.
- Threat Assessment:
- Once risks are identified, the next step is to assess these threats. This involves analyzing the likelihood of each risk materializing and its potential impact.
- Threat assessment requires staying informed about the latest cyber threat intelligence and understanding how different types of attacks (e.g., ransomware, phishing) can impact the organization.
- Vulnerability Analysis:
- This component focuses on identifying and evaluating vulnerabilities within the organization’s systems and networks. It involves regular security audits, penetration testing, and assessments to find weaknesses that could be exploited by cybercriminals.
- Impact Analysis:
- CRQ requires a detailed analysis of the potential impact of cyber threats. This includes financial losses, reputational damage, operational disruptions, and legal consequences.
- Impact analysis often requires input from various departments to understand the full scope of potential damages.
- Risk Evaluation:
- This process involves ranking and prioritizing identified risks based on their likelihood and potential impact. This helps in focusing resources and efforts on the most significant threats.
- Risk evaluation often involves categorizing risks into high, medium, or low priority.
- Mitigation Strategies:
- Based on the risk evaluation, appropriate risk mitigation strategies are developed. This can include strengthening cybersecurity defenses, implementing new policies, or investing in cyber insurance.
- Mitigation also involves preparing response plans for potential cyber incidents.
Conceptual Frameworks Underpinning CRQ
Understanding Cyber Events
Cyber Risk Quantification (CRQ) heavily relies on understanding various cyber events and their implications. This understanding forms the foundation of the entire CRQ process. Key cyber events include:
- Malware: Software designed to disrupt, damage, or gain unauthorized access to systems. In CRQ, identifying malware threats is crucial for protecting system integrity and ensuring data security.
- Data Breaches: Incidents where confidential information is accessed without authorization. Understanding the likelihood and potential impact of data breaches is vital for maintaining data confidentiality and trust.
- Phishing: Deceptive attempts to obtain sensitive information by impersonating trustworthy entities. Recognizing phishing risks helps in safeguarding data integrity and user awareness.
Each of these events carries distinct risks and requires tailored mitigation strategies, making their understanding fundamental to the CRQ process.
The CIA Framework

The CIA Framework aids in assessing the impact of cyber threats by prioritizing the protection of the following three principles:
- Confidentiality: Ensuring that sensitive information is accessed only by authorized parties. In CRQ, confidentiality is crucial for preventing unauthorized data breaches and maintaining trust.
- Integrity: Preserving the accuracy and reliability of data. Integrity in CRQ involves safeguarding data from unauthorized changes and ensuring the validity of information used in decision-making.
- Availability: Ensuring that information and resources are accessible when needed. CRQ considers the impact of cyber events on system availability critical for maintaining business continuity.
The Golden Triangle of CRQ
The Golden Triangle – Resilience, Frequency, and Severity – offers a strategic model for CRQ:
- Resilience: Resilience is how well an organization can resist and bounce back from cyber-attacks. This involves having strong defense mechanisms (like firewalls or antivirus software) and a good plan to recover if an attack does happen.
- Frequency: In CRQ, frequency is used to estimate how often cyber threats might occur. This helps organizations decide where to focus their efforts and resources.
- Severity: The potential impact of a cyber event. In CRQ, severity assessment guides the focus on high-impact risks and informs mitigation strategies.
So, in simpler terms, the Golden Triangle of CRQ is about asking three questions:
- How strong are our defenses (Resilience)?
- How often are we likely to face threats (Frequency)?
- What’s the worst that could happen (Severity)?
Integrating Operational Steps with Conceptual Frameworks
The operational steps in CRQ are informed and guided by these conceptual frameworks:
- Risk Identification and Cyber Events: The process of risk identification is deeply rooted in understanding various cyber events. For example, recognizing the potential of phishing attacks informs the development of targeted cybersecurity training programs.
- Threat Assessment and the CIA Framework: During threat assessment, the CIA framework provides a lens to evaluate the impact of threats on confidentiality, integrity, and availability. This guides decision-making on what cybersecurity controls to implement.
- Vulnerability Analysis and Resilience: While conducting vulnerability analyses, the concept of resilience helps in determining the robustness of current cybersecurity measures and planning for improvements.
- Impact Analysis and Severity: The severity aspect of the Golden Triangle is crucial during impact analysis. It helps in understanding the potential repercussions of cyber events on the organization’s operations and reputation.
- Risk Evaluation and Frequency: The frequency component aids in the risk evaluation process by determining how often a particular threat might occur, thereby prioritizing risks that require immediate attention.
How Do You Calculate Cyber Risk in Financial Terms?
Calculating cyber risk in financial terms involves a combination of various factors, including threat analysis, vulnerability assessment, probability of occurrence analysis, impact determination, and control analysis. There are two main approaches to this: the qualitative approach and the quantitative approach.
- Qualitative Approach in CRQ: The qualitative analysis in CRQ employs ordinal scales (like 1–5 or color-coded systems) to categorize risks based on frequency and impact. This approach, exemplified by frameworks like the NIST Cybersecurity Framework (CSF) and ISO 27005, allows organizations to gauge the severity of risks visually. These frameworks are particularly useful in scenarios where precise data may be lacking, enabling a relative risk assessment based on expert judgment.
- Quantitative Approach in CRQ: Conversely, quantitative analysis aims to assign specific numerical values to risk elements. Methods such as Bowtie Analysis, Probability/Impact Analysis, and Monte Carlo simulations provide a more exact risk quantification. These methods are beneficial in deriving a mathematical risk estimate, offering a detailed and objective risk perspective that aids in precise decision-making.
While both approaches have their merits, the quantitative approach in CRQ provides a more detailed, objective, and actionable analysis of cyber risks. It empowers organizations to make informed decisions, optimize their cybersecurity investments, and enhance their overall cybersecurity posture.
Breaking Down the Cyber Risk Calculation Process
The fundamental formula for risk in cybersecurity is:
Risk = Likelihood * Impact
- Likelihood refers to the probability of a threat exploiting a vulnerability. It is determined by considering the presence of threats and vulnerabilities in the system.
- Impact is the potential consequence or the extent of damage that can be caused if a threat successfully exploits a vulnerability. It can be in terms of financial, operational, or reputational loss.
- Risk is the potential for loss, damage, or destruction of an asset as a result of a threat exploiting a vulnerability.
Breach likelihood is calculated based on several factors, including vulnerability severity, threat level, asset exposure, and security controls.
- Vulnerability Severity: It refers to the seriousness of a weakness in a system that could be exploited by a threat. The severity of a vulnerability can range from low to critical.
- Threat Level: This is an assessment of the potential danger posed by a threat actor or event. Threat levels are often categorized as low, medium, high, or critical.
- Asset Exposure: This refers to the degree to which an asset is exposed to potential threats. The more exposed an asset is, the higher the likelihood of a breach.
- Security Controls: These are measures put in place to protect against threats and reduce the likelihood of a breach. Effective security controls can significantly lower the breach likelihood.
The OWASP Risk Rating Methodology provides a comprehensive approach to estimating the likelihood of a breach.
Popular Methods Used to Quantify Cyber Risk
FAIR Model
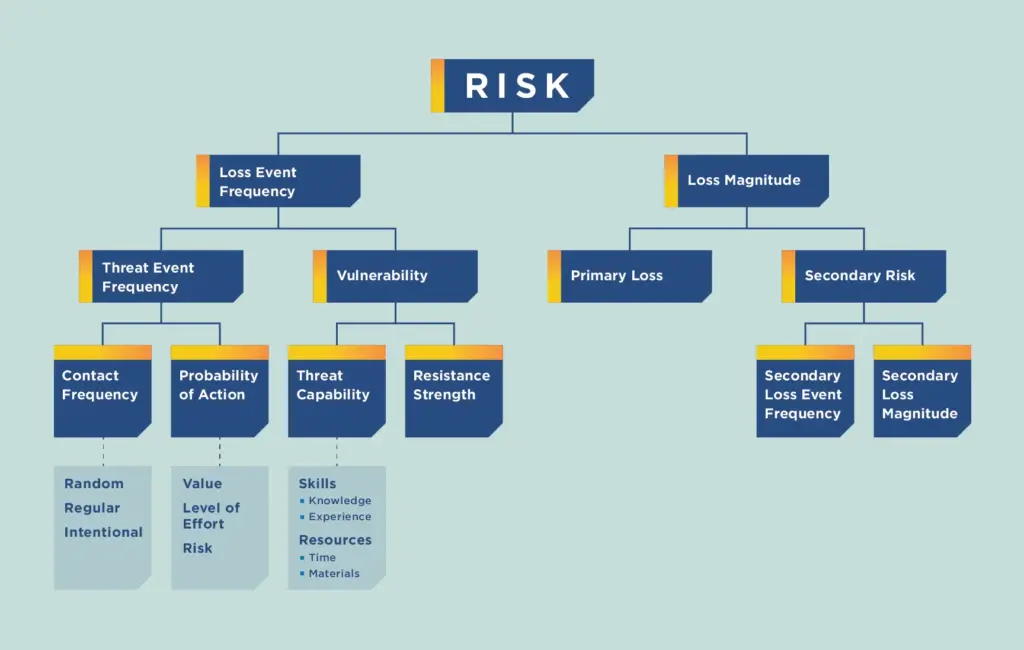
The Factor Analysis of Information Risk (FAIR) model, a pioneering methodology developed by the FAIR Institute, stands out as the only international standard quantitative model for information security and operational risk. It is unique in its approach, providing an open-source framework for understanding, analyzing, and quantifying information risk in financial terms.
Unlike traditional cyber risk assessments such as those from NIST and ISO, which effectively identify necessary security controls, FAIR addresses a critical gap: the financial analysis of cyber risks. Traditional models often delegate the task of quantifying the potential financial impacts of cyber incidents to the organizations themselves. FAIR fills this void by integrating a financial quantification layer into these frameworks, enhancing their capabilities in risk management.
FAIR breaks down the risk into two core components: the probable magnitude of financial loss and the frequency of such losses in various scenarios. By assessing both the likelihood and potential severity of financial impacts, FAIR assigns a specific dollar value to each cyber risk.
The FAIR model employs sophisticated data modeling techniques, including Monte Carlo simulations, to analyze and visualize complex risk scenarios. This statistical approach allows for a nuanced understanding of risk exposure, presenting a probabilistic forecast of potential losses, which aids in strategic decision-making.
Beyond risk quantification, FAIR provides a comprehensive framework for cyber risk management. It establishes a standard taxonomy and ontology for information and operational risk. This foundation aids in formulating data collection criteria and setting measurement scales for various risk factors.
Other popular methods
- Turnkey Cyber Risk Modeling: Automated, turnkey cyber risk modeling is an alternative method to FAIR. A good example of such a model is Bitsight Financial Quantification for Enterprise Cyber Risk. Using Bitsight for CRQ, you can streamline the process of quantifying your cyber risk financially – without investing in any additional headcount or resources.
- Monte Carlo Simulation: This is a statistical technique that allows for a distribution of potential outcomes and the probabilities they will occur. It is used in risk assessment to predict the likelihood of certain results.
- Framework-based Solutions: These are solutions built on established frameworks like the NIST Risk Management Framework. They provide a structured approach to identifying, assessing, and managing cyber risk.
Best Practices for Cyber Risk Quantification
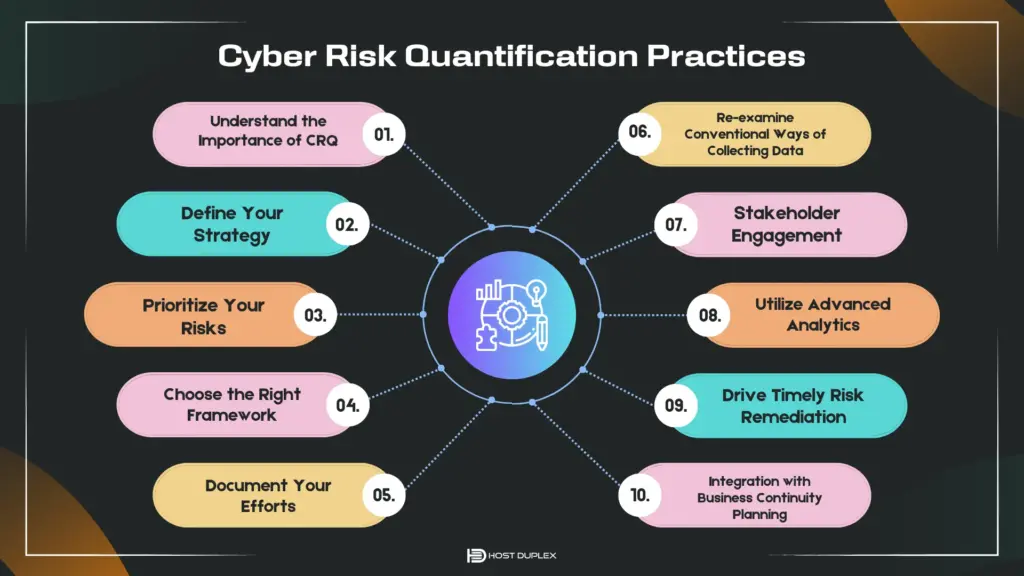
1. Understand the Importance of CRQ
Cyber risks have risen to the top of the list of threats to business prospects. In a survey conducted by Harvard Business Review Analytic Services, 74% of respondents named cyber risk as one of the top three risks their companies face. Therefore, understanding and quantifying these risks is crucial for any business.
2. Define Your Strategy
Before you get started with CRQ, you need to define a strategy for measuring and quantifying risk. This involves communicating with your teams to define your cybersecurity efforts in the context of CRQ.
3. Prioritize Your Risks
Assign criticality ratings for all your assets and determine the probabilities that each will be impacted by a malware attack. By determining the likely financial impact of different threats, you can direct finite resources to fend off the greatest threats.
4. Choose the Right Framework
There are two leading cyber risk quantification methods or frameworks: Factor Analysis of Information Risk (FAIR) and turnkey cyber risk modeling. FAIR is a model for understanding, analyzing, and quantifying cyber risk in any organization. On the other hand, turnkey cyber risk modeling, such as Bitsight Financial Quantification for Enterprise Cyber Risk, can streamline the process of quantifying your cyber risk financially.
5. Document Your Efforts
Document all your efforts. This includes collecting data effectively by pulling information about the sources of potential threats. Quantifying cyber risk requires a heavy reliance on data. Collect and analyze data from past incidents, industry benchmarks, and current security measures. Tools like SIEM (Security Information and Event Management) can provide valuable insights into your risk landscape.
6. Stakeholder Engagement
Involve stakeholders from various departments in the risk quantification process. Their insights can provide a more comprehensive view of the risk landscape and aid in developing more effective mitigation strategies.
7. Re-examine Conventional Ways of Collecting Data
To drive business action with CRQ results, re-examine conventional ways of collecting data. This involves building a comprehensive inventory of your information assets and knowing where data is stored, transported, and processed.
8. Utilize Advanced Analytics
Leverage advanced analytics to understand the probability and impact of potential cyber incidents. Machine learning algorithms can predict future threats based on historical data, aiding in more accurate risk quantification.
9. Drive Timely Risk Remediation
Determine the necessity for scenario-based analysis and drive timely risk remediation. This will help you manage the gravest risks.
10. Integration with Business Continuity Planning
Integrate cyber risk quantification into your overall business continuity planning. This ensures that cyber risks are considered in the broader context of business operations and resilience strategies.
Emerging Trends in Cyber Risk Quantification
Cyber Risk Quantification (CRQ) is evolving rapidly with the advent of new technologies and methodologies. Here are some of the emerging trends in CRQ:
Use of Artificial Intelligence (AI) and Machine Learning (ML) for Predictive Analytics
AI and ML are revolutionizing the field of CRQ by enabling the analysis of vast amounts of threat intelligence data. These technologies can identify emerging threats, patterns, and attack vectors and are being used for holistic cybersecurity risk management, proactive and accurate assessment of cyber risk posture, real-time detection and speedy prevention of cybercrime, and combating novel polymorphic and metamorphic cyberattacks.
Integration of CRQ with Cybersecurity Insurance and Risk Transfer Mechanisms
CRQ is increasingly being used for cyber insurance or compliance reporting. By quantifying cyber risks, organizations can figure out where to focus their cybersecurity efforts to make their enterprise an attractive candidate for a quality cyber insurance policy. Moreover, if organizations can lower their financial risk through effective CRQ, they might be able to save money on their policy.
Adoption of Cloud-Based CRQ Platforms for Scalability and Efficiency
The adoption of cloud-based CRQ platforms is on the rise due to their scalability and efficiency. Cloud services offer many benefits, including reduced costs, improved service quality, increased flexibility, and access to the newest technologies and innovations. However, simply moving IT systems to the cloud—“lift-and-shift”—will not automatically yield all the benefits that cloud infrastructure and systems can provide. Therefore, organizations need to approach cloud adoption as part of a holistic strategy to pursue digital transformation. For example, Salesforce, Microsoft Dynamics 365, HubSpot, Oracle NetSuite, and Zoho CRM are some of the top cloud-based CRM software of 2023.
How Are Organizations Transforming Their Cybersecurity with Cyber Risk Quantification: Real-World Examples
Several organizations have effectively leveraged Cyber Risk Quantification to bolster their cybersecurity strategies. Here are a couple of notable examples demonstrating its effective implementation:
- ISACA’s Strategic CRQ Approach: ISACA, a leading professional association in IT governance and cybersecurity, undertook a comprehensive cyber risk quantification initiative. They started by identifying key risk scenarios and developing detailed risk profiles. Utilizing established frameworks like COBIT and the Factor Analysis of Information Risk (FAIR), they were able to assess risks and craft optimal remediation strategies. The incorporation of machine learning algorithms played a crucial role in minimizing subjectivity and accelerating the risk management process, leading to more robust and agile cybersecurity practices.
Source: ISACA’s Cyber Risk Report - University of Wollongong’s Innovative Cyberquantification Platform: At the University of Wollongong, the development of a machine learning-based cyberquantification platform marked a significant advancement in cybersecurity management. This platform underpins their governance, risk, and compliance software-as-a-service solution, myRISK, offering a sophisticated and proactive approach to risk quantification and management.
Source: University of Wollongong Cybersecurity Case Study
These examples demonstrate how organizations can successfully implement CRQ to understand their cyber risk exposure better, optimize their cybersecurity investments, and enhance their overall cybersecurity posture. It’s important to note that the specifics of implementing CRQ can vary based on the organization and the nature of the threats it faces. Always consult with a cybersecurity professional for advice tailored to your specific circumstances.



Cyber Risk Quantification Guide: Measurement & Mitigation